This post by David Papkin Configuring Role-Based Administration in SCCM 2012 R2
Microsoft® System Center 2012 Configuration Manager and System Center 2012 R2 Configuration Manager implement role-based access control (RBAC). With RBAC, you can use security roles, security scopes, and collections to define access permissions for your administrative users.
Overview of Role-Based Administration
You can use role-based administration in Configuration Manager to centrally define security settings and to delegate administrative tasks to users or groups. You can assign an administrative user one or more security roles that represent a set of administration tasks. The security role includes all permissions necessary to complete the tasks that relate to the role. For example, you can assign the Application Deployment Manager security role to a user who will manage application deployments. This role automatically grants permissions to deploy applications to computer devices or users.You can further define the objects that a security role can administer, thereby limiting administrative access to specific collections and security scopes. You can use a security scope to associate specific objects with one or more administrative users. For example, you can give an administrator permission to deploy
only specific applications by associating those applications with a security scope, instead of permissions to deploy all applications.
Administrative users can see only the objects that they have permission to manage, which the security role, security scope, and collection define.
You can use the built-in security roles and scopes, or you can create your own custom security settings to use throughout the hierarchy. When you create administrative users, you configure and replicate security assignments throughout the central administration site and the hierarchy’s primary sites.
Security Roles
A security role is a group of permissions that are necessary for performing specific administrative tasks. The role consists of individual permissions for each object type that an administrative user is allowed to manage. For example, the Application Administrator role
has a cumulative set of permissions that define its security role. This role consists of a set of
individual permissions to manage a variety of objects, including the following permissions for
application objects:
• Approve
• Create
• Delete
• Modify
• Modify Folder
• Move Object
• Read
• Modify Report
• Set Security Scope
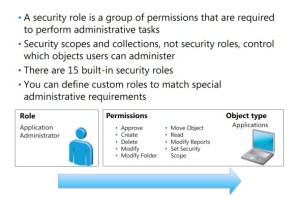
A security role is a group of permissions that are necessary for performing specific administrative tasks. The role consists of individual permissions for each object type that an administrative user is allowed to manage.
You can use scopes and collections to limit access by administrative users to individual object instances because the roles themselves do not specify user permissions for individual objects.
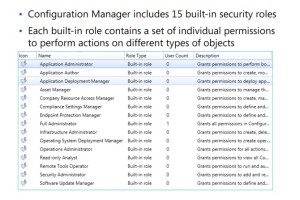
Configuration Manager includes 15 built-in roles that include permissions for executing typical tasks on different types of objects. You cannot modify or delete the built-in roles, but you can create custom roles to match special administrative requirements.
Built-In Roles
Configuration Manager includes the 15 built-in security roles that the following table lists. Each
role gives specific permissions to an administrative user to perform actions on certain types of
objects.
Planning Role-Based Administration
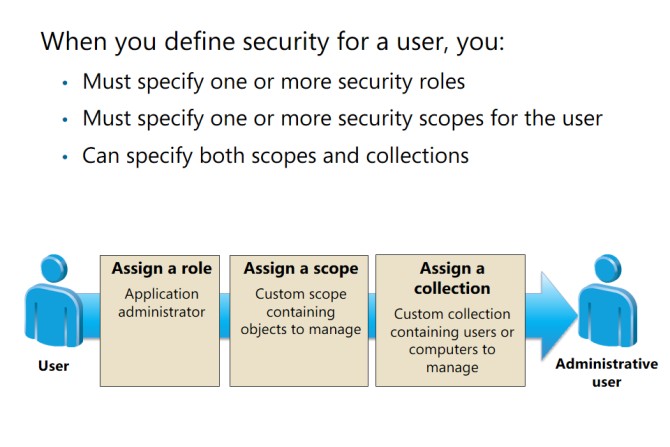
Configuring role-based administration requires careful consideration. When you plan to add an
administrative user, you must consider the security roles, security scopes, and collections.
When planning security configuration, consider the following factors:
• Security roles control what you allow an administrative user to do.
• Security scopes control the securable Configuration Manager objects that the
administrative user can administer.
• Collections control the users and devices that an administrative user can manage.
• You must assign an administrative user to at least one security scope.
• You can map each administrative user to separate security scopes and collections.
This video Planning and Configuring Role Based Administration in SCCM 2012 R2 by David Papkin
This concludes this post by David Papkin Configuring Role-Based Administration in SCCM 2012 R2