This post by David Papkin is about securing privileged access. It applies to Microsoft Server 2016
Link to original Microsoft article Securing Privileged Access. Portion of it is printed below.
Securing privileged access is a critical first step to establishing security assurances for business assets in a modern organization. The security of most or all business assets in an organization depends on the integrity of the privileged accounts that administer and manage IT systems. Cyber-attackers are targeting these accounts and other elements of privileged access to rapidly gain access to targeted data and systems using credential theft attacks like Pass-the-Hash and Pass-the-Ticket.
Protecting administrative access against determined adversaries requires you to take a complete and thoughtful approach to isolate these systems from risks. This figure depicts the three stages of recommendations for separating and protecting administration in this roadmap:
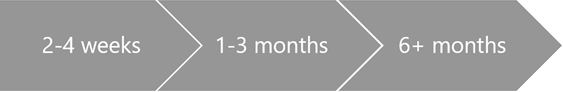
Roadmap Objectives:
- 2-4 week plan: quickly mitigate the most frequently used attack techniques
- 1-3 month plan: build visibility and control of admin activity
- 6+ month plan: continue building defenses to a more proactive security posture
Microsoft recommends you follow this roadmap to secure privileged access against determined adversaries. You may adjust this roadmap to accommodate your existing capabilities and specific requirements in your organizations.
Note
Securing privileged access requires a broad range of elements including technical components (host defenses, account protections, identity management, etc.) as well as changes to process, and administrative practices and knowledge.
Why is Securing Privileged Access important?
In most organizations, the security of most or all business assets depends on the integrity of the privileged accounts that administer and manage IT systems. Cyber-attackers are focusing on privileged access to systems like Active Directory to rapidly gain access to all of an organizations targeted data.
Traditional security approaches have focused on using the ingress and egress points of an organizations network as the primary security perimeter, but the effectiveness of network security has been significantly diminished by two trends:
- Organizations are hosting data and resources outside the traditional network boundary on mobile enterprise PCs, devices like mobile phones and tablets, cloud services, and BYOD devices
- Adversaries have demonstrated a consistent and ongoing ability to obtain access on workstations inside the network boundary through phishing and other web and email attacks.
The natural replacement for the network security perimeter in a complex modern enterprise is the authentication and authorization controls in an organization’s identity layer. Privileged administrative accounts are effectively in control of this new “security perimeter” so it’s critical to protect privileged access:
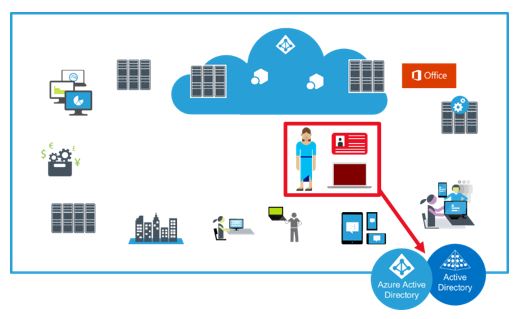
An adversary that gains control of an administrative account can use those privileges to pursue their gain at the expense of the target organization as depicted below:
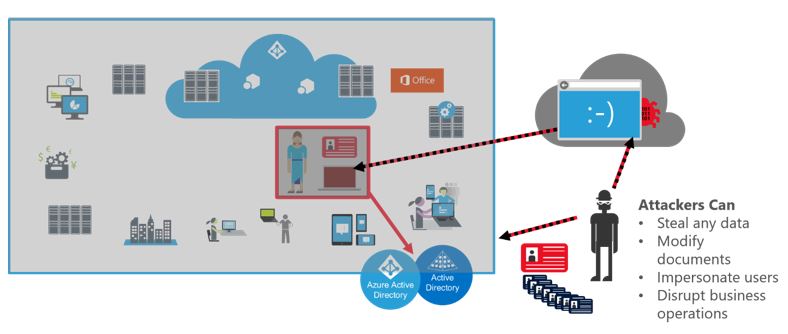
For more information on the types of attacks that commonly lead to attackers in control of administrative accounts, please visit the Pass The Hash web site for informative white papers, videos and more.
This figure depicts the separate “channel” for administration that the roadmap establishes to isolate privileged access tasks from high risk standard user tasks like web browsing and accessing email.
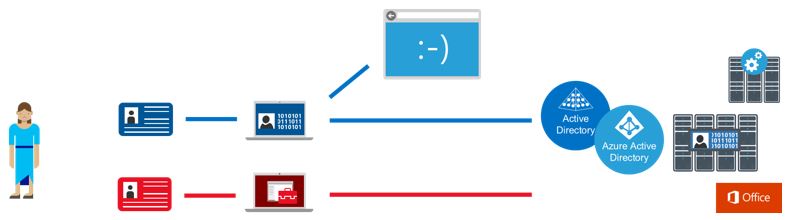
Because the adversary can gain control of privileged access using a variety of methods, mitigating this risk requires a holistic and detailed technical approach as outlined in this roadmap. The roadmap will isolate and harden the elements in your environment that enable privileged access by building mitigations in each area of the defense column in this figure:
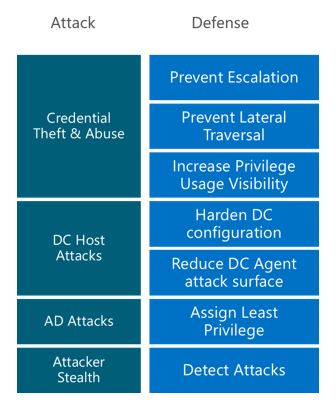
Security privileged access roadmap
The roadmap is designed to maximize the use of technologies that you already have deployed, take advantage of key current and upcoming security technologies, and integrate any 3rd party security tools you may already have deployed.
The roadmap of Microsoft recommendations is broken into 3 stages:
- 2-4 week plan – Quickly mitigate the most frequently used attack techniques
- 1-3 month plan – Build visibility and control of admin activity
- 6+ month plan – Continue building defenses to a more proactive security posture
Each stage of the roadmap is designed to raise the cost and difficulty for adversaries to attack privileged access for your on-premises and cloud assets. The roadmap is prioritized to schedule the most effective and the quickest implementations first based on our experiences with these attacks and solution implementation.
Note
The timelines for the roadmap are approximate and are based on our experience with customer implementations. The duration will vary in your organization depending on the complexity of your environment and your change management processes.
Security Privileged Access Roadmap: Stage 1
Stage 1 of the roadmap is focused on quickly mitigating the most frequently used attack techniques of credential theft and abuse. Stage 1 is designed to be implemented in approximately 2-4 weeks and is depicted in this diagram:
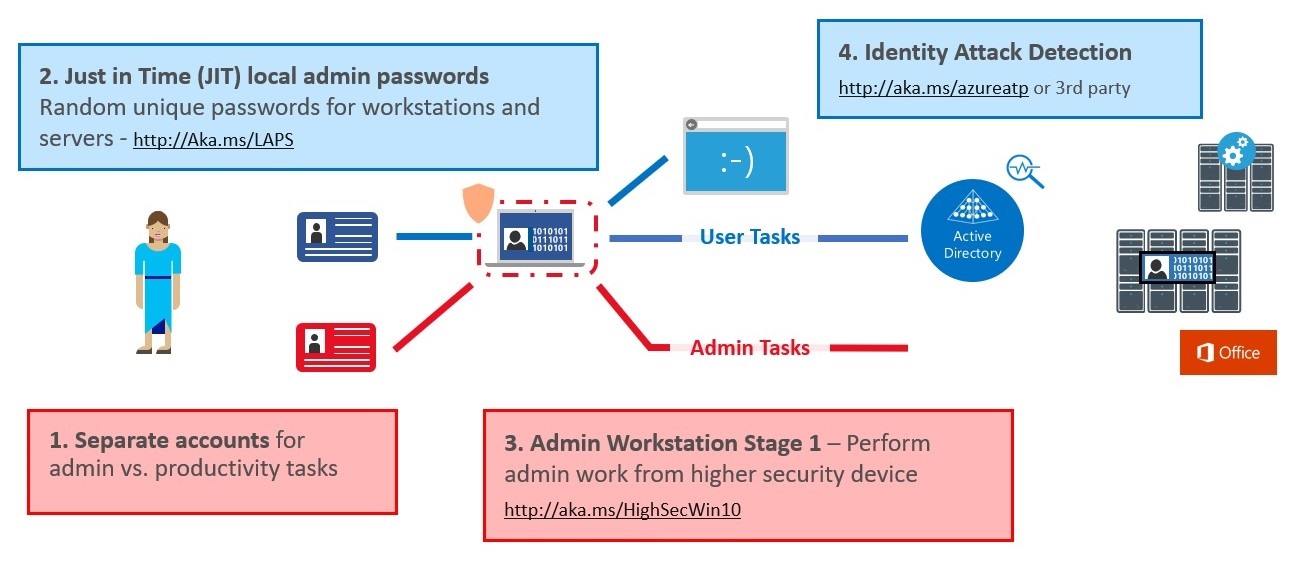
Stage 1 of the Security Privileged Access roadmap includes these components:
1. Separate Admin account for admin tasks
To help separate internet risks (phishing attacks, web browsing) from administrative privileges, create a dedicated account for all personnel with administrative privileges. Additional guidance on this is included in the PAW instructions published here.
2. Privileged Access Workstations (PAWs) Phase 1: Active Directory admins
To help separate internet risks (phishing attacks, web browsing) from domain administrative privileges, create dedicated privileged access workstations (PAWs) for personnel with AD administrative privileges. This is the first step of a PAW program and is Phase 1 of the guidance published here.
3. Unique Local Admin Passwords for Workstations
4. Unique Local Admin Passwords for Servers
To mitigate the risk of an adversary stealing a local administrator account password hash from the local SAM database and abusing it to attack other computers, you should use the LAPS tool to configure unique random passwords on each workstation and server and register those passwords in Active Directory. You can obtain the Local Administrator Password Solution for use on workstations and servers here.
Additional guidance for operating an environment with LAPS and PAWs can be found here.
Security Privileged Access Roadmap: Stage 2
Stage 2 builds on the mitigations from Stage 1 and is designed to be implemented in approximately 1-3 months. The steps of this stage are depicted in this diagram:
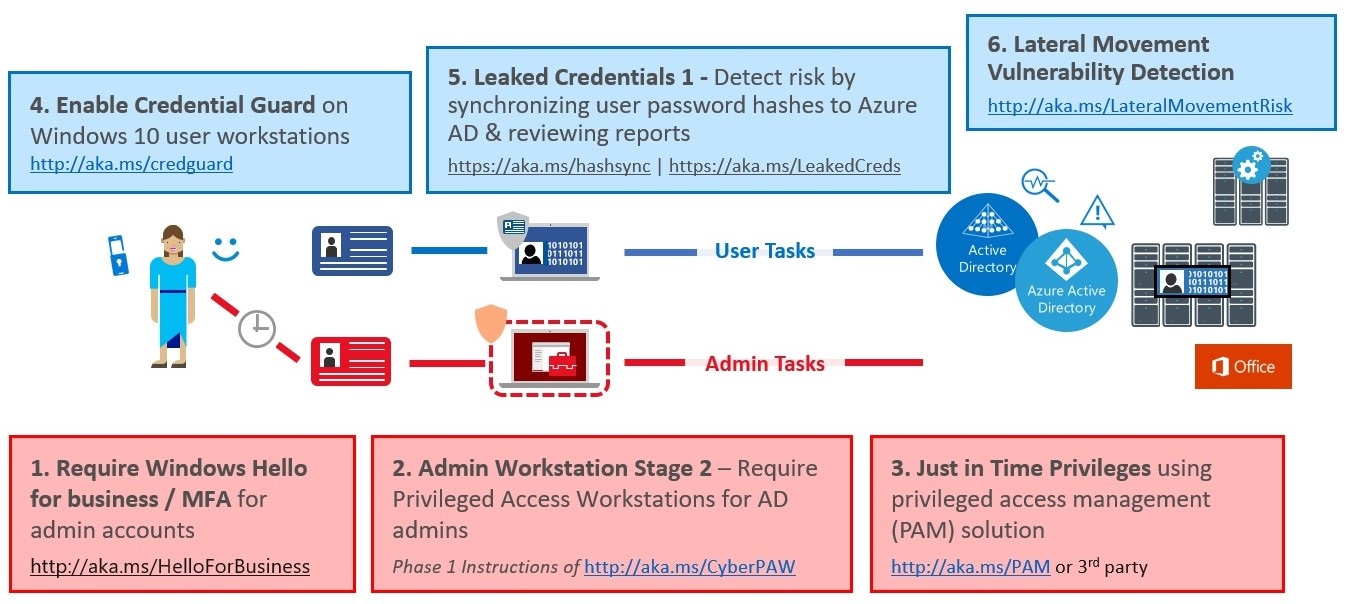
1. PAW Phases 2 and 3: all admins and additional hardening
To separate internet risks from all privileged administrative accounts, continue with the PAW you started in stage 1 and implement dedicated workstations for all personnel with privileged access. This maps to Phase 2 and 3 of the guidance published here.
2. Time-bound privileges (no permanent administrators)
To lower the exposure time of privileges and increase visibility into their use, provide privileges just in time (JIT) using an appropriate solution such as the ones below:
- For Active Directory Domain Services (AD DS), use Microsoft Identity Manager (MIM)’s Privileged Access Manager (PAM)capability.
- For Azure Active Directory, use Azure AD Privileged Identity Management (PIM) capability.
3. Multi-factor for time-bound elevation
To increase the assurance level of administrator authentication, you should require multi-factor authentication before granting privileges. This can be accomplished with MIM PAM and Azure AD PIM using Azure Multi-factor authentication (MFA).
4. Just Enough Admin (JEA) for DC Maintenance
To reduce the quantity of accounts with domain administration privileges and associated risk exposure, use the Just Enough Administration (JEA) feature in PowerShell to perform common maintenance operations on domain controllers. The JEA technology allows specific users to perform specific administrative tasks on servers (like Domain Controllers) without giving them administrator rights. Download this guidance from TechNet.
5. Lower attack surface of Domain and DCs
To reduce opportunities for adversaries to take control of a forest, you should reduce the pathways an attacker can take to gain control of Domain Controllers or objects in control of the domain. Follow guidance to reduce this risk published here.
6. Attack Detection
To get visibility into active credential theft and identity attacks so that you can respond quickly to events and contain damage, deploy and configure Microsoft Advanced Threat Analytics (ATA).
Prior to installing ATA, you should ensure you have a process in place to handle a major security incident that ATA may detect.
- For more information on setting up an incident response process, see Responding to IT Security Incidents and the “Respond to suspicious activity” and “Recover from a breach” sections of Mitigating Pass-the-Hash and Other Credential Theft, version 2.
- For more information on engaging Microsoft services to assist with preparing your IR process for ATA generated events and deploying ATA, contact your Microsoft representative by accessing this page.
- Access this page for more information on engaging Microsoft services to assist with investigating and recovering from an incident.
- To Implement ATA, follow the deployment guide available here.
Security Privileged Access Roadmap: Stage 3
Stage 3 of the roadmap builds on the mitigations from Stages 1 and 2 to strengthen and add mitigations across the spectrum. Stage 3 is depicted visually in this diagram:
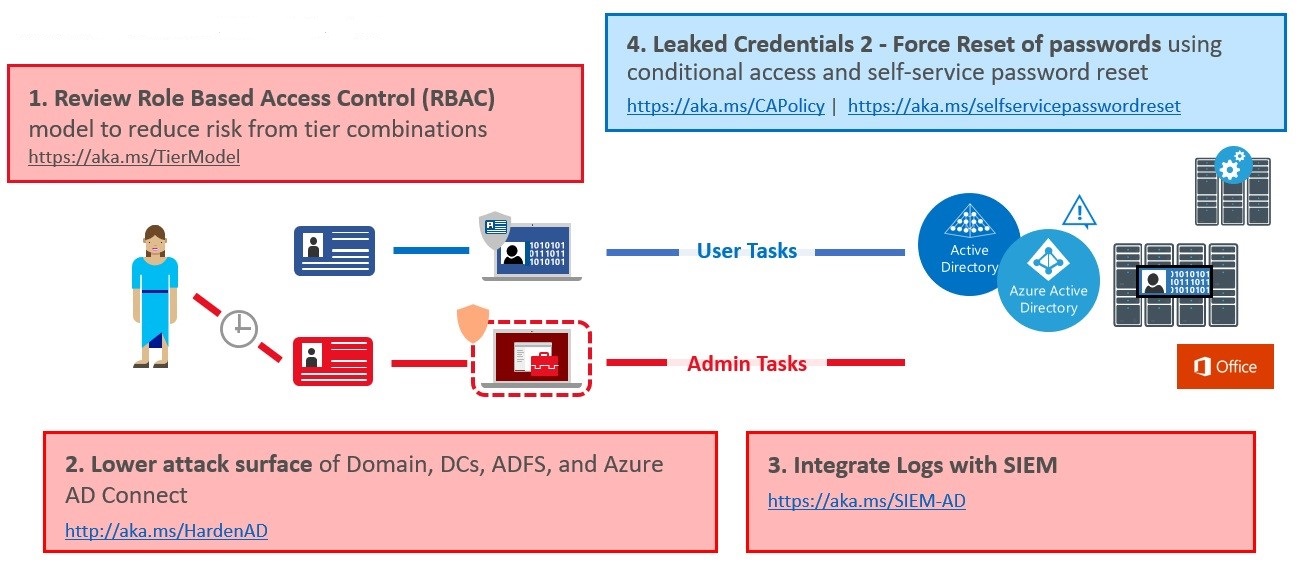
These capabilities will build on the mitigations from previous phases and move your defenses into a more proactive posture.
1. Modernize Roles and Delegation Model
To reduce security risk, you should redesign all aspects of your roles and delegation model to be compliant with the rules of the tier model, accommodate cloud service administrative roles, and incorporate administrator usability as a key tenet. This model should leverage the JIT and JEA capabilities deployed in the earlier stages as well as task automation technology to achieve these goals.
2. Smartcard or Passport Authentication for all admins
To increase the assurance level and usability of administrator authentication, you should require strong authentication for all administrative accounts hosted in Azure Active Directory and in your Windows Server Active Directory (including accounts federated to a cloud service).
3. Admin Forest for Active Directory administrators
To provide the strongest protection for Active Directory administrators, set up an environment that has no security dependencies on your production Active Directory and is isolated from attacks from all but the most trusted systems in your production environment. For more information on the ESAE architecture visit this page.
4. Windows Defender Device Guard for DCs (Server 2016)
To limit the risk of unauthorized programs on your domain controllers from adversary attack operations and inadvertent administrative errors, configure Windows Defender Device Guard virtualization-based security for kernel (also known as Hypervisor Code Integrity, HVCI) and Windows Defender Application Control policies (also known as Configurable Code Integrity, Configurable CI) for applications to only allow authorized executables to run on the machine. For more information on Windows Defender Device Guard visit this page.
5. Shielded VMs for virtual DCs (Server 2016 Hyper-V Fabric)
To protect virtualized domain controllers from attack vectors that exploit a virtual machine’s inherent loss of physical security, use this new Server 2016 Hyper-V capability to help prevent the theft of Active Directory secrets from Virtual DCs. Using this solution, you can encrypt Generation 2 VMs to protect the VM data against inspection, theft, and tampering by storage and network administrators as well as harden the access to the VM against Hyper-V host administrators attacks. For more information on Shielded VMs visit this page.
End of David Papkin post.
David Papkin favorite movies
Ava Gardner in Singapore (Flim Noir)