This page by David Papkin has information on EC-Council CEH course.
The Certified Ethical Hacker (CEH) program is the most comprehensive ethical hacking course on the globe to help information security professionals grasp the fundamentals of ethical hacking.
To master the hacking technologies, you will need to become one, but an ethical one! The accredited hacking course provides the advanced hacking tools and techniques used by hackers and information security professionals alike to break into an organization. As we put it, “To beat a hacker, you need to think like a hacker”.
Your guide to Ethical Hacking from home.
CEH classroom attack website (www.certifiedhacker.com)
Terminology
C2M2 – The Cybersecurity Capability Maturity Model (C2M2) is a free, user-friendly tool that enables organizations to voluntarily measure the maturity of their cybersecurity capabilities. The C2M2 can help organizations of all sectors, types, and sizes to evaluate and make improvements to their cybersecurity programs and strengthen their operational resilience.
Defense in Depth – Security strategy in which several protection layers are placed throughout an information system
Enumeration – The attacker establishes an active connection with the victim and try to discover as much attack vectors as possible, which can be used to exploit the systems further.
Enumeration can be used to gain information on −
- Network shares
- SNMP data, if they are not secured properly
- IP tables
- Usernames of different systems
- Passwords policies lists
Enumerations depend on the services that the systems offer. They can be −
- DNS enumeration
- NTP enumeration
- SNMP enumeration
- Linux/Windows enumeration
- SMB enumeration
5 phases of Hacking
- Reconnaissance – Preparatory phase where an attacker seeks to gather information about a target prior to launching an attack.
- Scanning – Scans the network based on information gathered during reconnaissance.
- Gaining Access – Hacker obtains access to the operating system or applications on the computer or network
- Maintaining Access – Hacker tries to retain his or her ownership of the system.
- Clearing Tracks – Hackers always cover their tracks to hide their identity.
Risk – Degree of uncertainty or expectation that an adverse event may cause damage to the system.
Vulnerability – Existence of a weakness, design or implementation error that can lead to an unexpected event compromising the security of the system.
Mobile
SQL Injection
SQL Injection Prevention Cheat Sheet
Advanced SQL Injection to Operating System Full Control (PDF)
OWASP Appsec Tutorial Series – Episode 2: Injection Attacks
Wireshark
Wireshark HTTPS (Has 9 learning Activities.Very good!))
https://wiki.wireshark.org/DisplayFilters
Understanding an Nmap Fingerprint
Healthcare ransomware attack: Prevention and backups are critical
Ten ways to stop a ransomware threat targeting healthcare data
How to Use SSH keys with Windows on Azure
Labs
Module 5
Lab 2 Nessus
#16 Must enter 10.10.10.16 for the Target before Save
#18 There is no User Defined tab
Click the Policy you created
Click Launch
Module 6
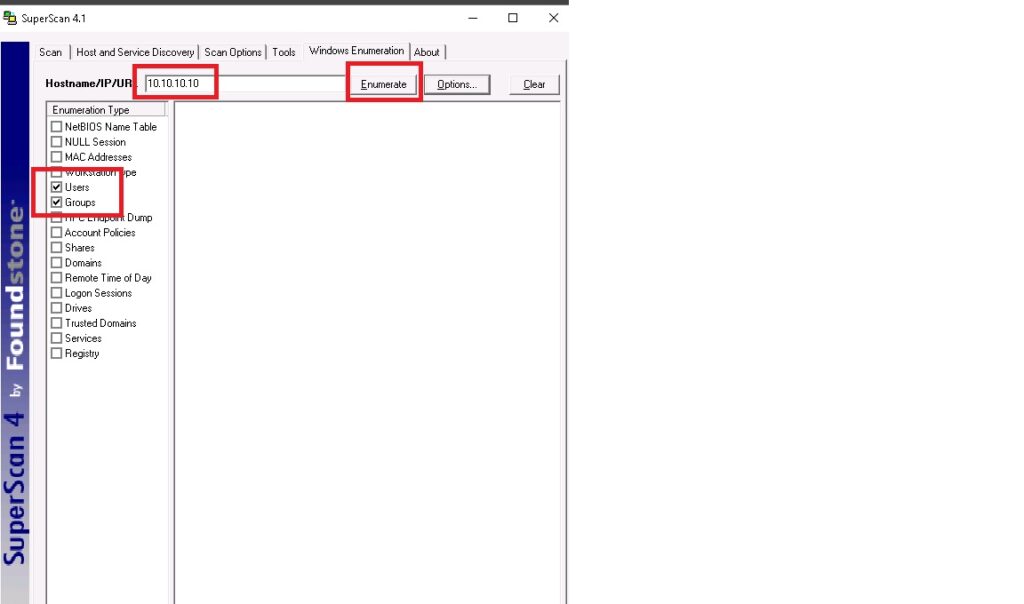
Superscan – Enumeration tool.
To list all the Users in the SAM database.
- Extract into Downloads folder
- Right-click and select Run as administrator
- Click on Windows Enumeration tab
- On the left hand side Window, in the Enumeration Type unselect everything but Users
- Put the IP address of the computer and click Enumerate
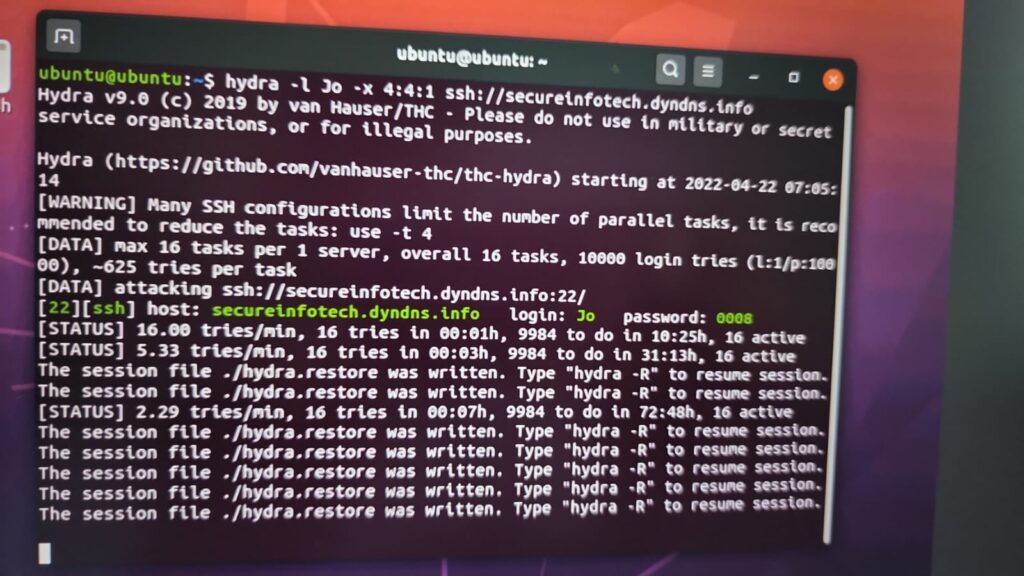
Hydra
Using hydra to crack linux passwords
Hydra is a parallelized login cracker which supports many common login protocols like forms on websites, FTP, SMB, POP3, IMAP, MySQL, VNC, SSH and others.
This tool makes it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely.
To find out the password of user “Jo” on an ssh enabled system.
- Login to Kali Linux
- Open terminal window
- “sudu apt-get install hydra” to install hydra package
- “hydra -l jo -x 4:4:1 ssh://secureinfotech.dyndns.info”
- The Password info will be highlighted in green
- Type “man hydra” for more info on hydra
Tutorial Install And Use THC Hydra On Kali Linux
https://www.kali.org/tools/hydra/
https://en.wikipedia.org/wiki/Hydra_(software)
Module 7
Lab 1 Task 1 njRAT trojan
#8 Save As – Save to D:\CEH-Tools instead of Desktop. This way , it will be accessible from Server 2016