Questions
Section 1
Q: What is a good security admin process to prevent Cyber-attack from occurring?
A:
- Every machine on the network should have an antivirus programme with current updates installed.
- Computers connected to the network should not have modems or have multiple NICS enabled or allow tethering to Mobile phone.
- Virus protection is installed on all user computers and servers.
- Laptops that are used for off-site work and then returned to the network are inspected by cybersecurity personnel before being allowed on the network.
- Prevent users from installing instant messenger and other types of software that create a security risk.
- Implement a strong and enforceable written policy concerning computer usage.
- Review firewall, proxy server and event logs frequently.
- Develop identified staff who need to become proficient in protecting the network.
- Close all ports that are not needed.
- Set up notification services to inform management if an event occurs.
Q: What controls are needed in a security program aligned with organization and security profiles? What permissions needed for RBAC for these controls?
A:
- Preventive controls – Start with a focus on preventive controls, including management of user’s access levels and entitlements, so as to keep irregularities from occurring. This prevent staff from performing activities that they should not perform.
- Detective controls – Subsequently, expand the identity and access management controls towards detective controls with access governance. This involves performing access certification on a recurring basis, monitoring privileged user activity to encourage adherence to policy and flagging any abnormal activity that may have occurred.
- Corrective controls – Ultimately, expand the identity and access management controls towards corrective controls. Corrective controls will correct errors that have been detected such as revoking access when abuse of privileges or over-credentialing is uncovered.
A:
- Establish a list of roles within the organization, assign the permission that is allowed for each role.
- User should not be assigned permission directly, rather acquire them through their role in the job.
- Management of individual user rights becomes a matter of simply assigning appropriate roles to the user account.
Q: What are some mitigations for phishing attacks?
A:
- Network activity monitoring
- Security awareness training
- Corporate policies and procedures
- Strong file and directory permissions
Q: What are some countermeasures against malicious code attacks?
A:
- Sandbox
- Change control
- Memory management
- Public-Key Infrastructure
Q:
Why should you identify users before allowing them access to a computer that is connected to a network?
A:
To prevent unauthorized persons from accessing the computer or network.
Q:
What is the purpose of a penetration test?
A:
Q: What is Discretionary Access Control?
A:
Q: How can users have different levels of access with different objects?
A:
Permissions can be used to enable different levels of access.
Q: What are some assessment metrics that may be used to assess a system’s potential threat vulnerability?
A:
- Determine the probability a system functions without breaches within a period of time. Once this is done, the system can then be classified as high, medium or low risk to ensure appropriate action can be taken. For example, high risk system will be reviewed more frequently, or have live monitoring system installed.
- Quantify the system’s available services.
- Identify the number of security flaws within the system.
- Measure the system’s integrity in the presence of failure.
- Establish the baseline of network traffic and compare to find out what is not normal
Q: What methods can be used to revise security administration plans and update staff because of new and evolving cybersecurity policies and security threats?
A:
- Assess the risk of the newly emerged security threats posing to the IT assets of the company. Once risk and potential impact to IT asset has been ascertained, understand how it works, then develop a countermeasure against it. Update the security administration plans with the information so it can be referred to when a breach through the security threat happens.
- Keep staff updated of new and updated cybersecurity policies and security threats through handouts, training or sharing sessions.
Q: How to implement NAT on a router to protect from an internet attack?
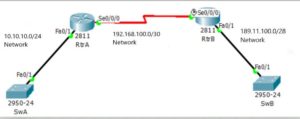
A:
- Enable NAT on RtrB.
- Set Se0/0/0 as Inside interface and Fa0/1 as Outside interface.
- Test translation.
Q: How can you monitor and control user access to a server room?
A:
Apply a False Acceptance Rate to prevent unauthorized persons from accessing the room
Section 2
Q: What is a good investigation process about any security breaches of network access?
A:
- Identify the system that has been breached and take it offline immediately.
- Examine the system and all its system and event logs to find out what was accessed and from where.
- Try and recover the messages that were deleted so the source of infection can be ascertained.
Q: What are some good countermeasures?
A:
- Implement a strict security policy to prevent students who are using the campus network from using almost all protocols except the web.
- Make sure all the systems sit in a different subnet from the users’ subnet, so as to reduce the chances of system breaches after a user’s device get infected.
- Strengthen the security protocol of the system that was breached.
- Perform penetration testing on the network to find any vulerabilities and take necessary actions on the findings.
- Make sure email messages that are deleted , are retained in the server for a period of time.
- Disable unused network ports.
V11
Q: What document should a pen-tester sign BEFORE doing any work at a company to insure confidentiality of the company’s information?
A: Non-Disclosure Agreement (NDA)
Q: What document should a pen-tester sign BEFORE doing any work at a company to insure legality of the pen-testing?
A: Rules of Engagement.
Q: Which scanning is popular to use NMAP for?
A: Port Scanning.
Q: What NMAP scan options will set TCP flags to PSH/FIN/URG ?
A: Xmas scan or Nmap-sX
Q: What is the difference of penetration testing vs vulnerability scanning?
A: Pen testing tests exploits vulnerabilities and vulnerability scans checks for weaknesses or flaws.
Q: List one tool for pen testing and one tool for vulnerability scan.
A: pen testing ( Metasploit, CANVAS, Core Impact, Brutus) and one tool for vulnerability scan(Nessus, Acunetix, OpenVas, SAINT, GFILANGUARD).
Q: What attacks can enabling Port Security help prevent?
A: ARP poisoning , MITM , Sniffing.
Q: What type of testing involves testing a system with no prior knowledge of its internal workings.?
A: Black box testing.
Q: If your IDS monitoring tool , such as Snort detected “LARGE ICMP PACKET” , what kind of attack might this be?
A: Ping of Death, DOS
Q: How could data theft be prevented from someone replying to a fake email?
A: Education and Security Policy.
Q: How does a firewall and an IDS deal with attacks?
A: IDS detects /alerts attacks but FW prevents or stops attacks.
Q: If a attacker put this code into a web browser ‘Insert int username values{‘1′,’1’}– ,
what type of attack is this? How to prevent it?
A: SQL Injection. Input Validation, Boundary checking, IDS/IPS
Q: Which wireless attack uses a fake Access Point with same name as legitimate AP?
A: Evil Twin, Honeypot AP, Rogue Access Point.
Q: What file format extension does Android use for app installation?
A; .apk
Q: What areas can an IoT device be attacked?
A: Software, Hardware, Network, Firmware.
Q: What cloud computing threats pertains to profiling risk?
A: Lack of risk assessment, Due Diligence.
Q: Which of the 3 tenets of security, cryptography cant provide?
A: Availability.
Q: How to identify the version of the web server?
A: Banner Grabbing, OS Fingerprinting
Q: Which vulnerability scanner scans applications on the web?
A: Web Application Scanner
Q: Which DOS technique uses oversized ping?
A: Ping of death.