This post by David Papkin about Managing Virtual Networks using Microsoft Azure
An Azure virtual network (VNet) is a representation of your own network in the cloud. It is a logical isolation of the Azure cloud dedicated to your subscription. You can fully control the IP address blocks, DNS settings, security policies, and route tables within this network. You can also further segment your VNet into subnets and launch Azure IaaS virtual machines (VMs) and/or Cloud services (PaaS role instances). Additonally you can connect the virtual network to your on-premises network using one of the connectivity options available in Azure. In essence, you can expand your network to Azure, with complete control on IP address blocks with the benefit of enterprise scale Azure provides.
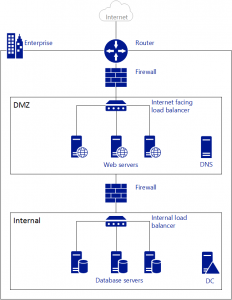
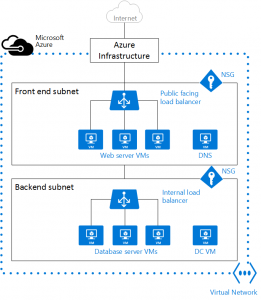
Diagram of on-premise vs azure network
Virtual Network Benefits
- Isolation. VNets are completely isolated from one another. That allows you to create disjoint networks for development, testing, and production that use the same CIDR address blocks.
- Access to the public Internet. All IaaS VMs and PaaS role instances in a VNet can access the public Internet by default. You can control access by using Network Security Groups (NSGs).
- Access to VMs within the VNet. PaaS role instances and IaaS VMs can be launched in the same virtual network and they can connect to each other using private IP addresses even if they are in different subnets without the need to configure a gateway or use public IP addresses.
- Name resolution. Azure provides internal name resolution for IaaS VMs and PaaS role instances deployed in your VNet. You can also deploy your own DNS servers and configure the VNet to use them.
- Security. Traffic entering and exiting the virtual machines and PaaS role instances in a VNet can be controlled using Network Security groups.
- Connectivity. VNets can be connected to each other, and even to your on-premises datacenter, by using a site-to-site VPN connection, or ExpressRoute connection. To learn more about VPN gateways, visit About VPN gateways. To learn more about ExpressRoute, visit ExpressRoute technical overview.
Note:
Make sure you create a VNet before deploying any IaaS VMs or PaaS role instances to your Azure environment. ARM based VMs require a VNet, and if you do not specify an existing VNet, Azure creates a default VNet that might have a CIDR address block clash with your on-premises network. Making it impossible for you to connect your VNet to your on-premises network.
Subnets
Subnet is a range of IP addresses in the VNet, you can divide a VNet into multiple subnets for organization and security. VMs and PaaS role instances deployed to subnets (same or different) within a VNet can communicate with each other without any extra configuration. You can also configure route tables and NSGs to a subnet.
IP addresses
There are two types of IP addresses assigned to resources in Azure: public and private. Public IP Addresses allow Azure resources to communicate with Internet and other Azure public-facing services like Azure Redis Cache, Azure Event Hubs. Private IP Addresses allows communication between resources in a virtual network, along with those connected through a VPN, without using an Internet-routable IP addresses.
To learn more about IP addresses in Azure, visit IP addresses in virtual network
Network Security Group (NSG)
You can create NSGs to control inbound and outbound access to network interfaces (NICs), VMs, and subnets. Each NSG contains one or more rules specifying whether or not traffic is approved or denied based on source IP address, source port, destination IP address, and destination port. To learn more about NSGs, visit What is a Network Security Group.
Implementing and Managing Virtual Networks
To create a virtual network, you can either use the full portal or upload a network configuration file. A network configuration file is an XML file with a specific schema.
You can also configure multiple network interface cards (NICs) for Azure VMs. In this case, each NIC receives a separate DIP and you can utilize the NICs to isolate communication. For more information about multiple NICs, see the following link:
Create a VM with Multiple NICs
http://go.microsoft.com/fwlink/?LinkID=522618
About VPN Devices for Virtual Network
http://go.microsoft.com/fwlink/?LinkID=522619
ExpressRoute is a service that enables Azure customers to create a dedicated connection to Azure, whichdoes not connect through the public Internet. This contrasts with VPNs, which use encryption to tunnel securely through the public Internet. Because ExpressRoute connections are dedicated, they can offer faster speeds, higher security, lower latencies, and higher reliability than VPNs.
To learn more about Express Route, see:
ExpressRoute Technical Overview
http://go.microsoft.com/fwlink/?LinkID=522620
Video Demo of Managing Virtual Network in Azure by David Papkin
For hands-on training, please contact your local training provider about schedules for the following Microsoft course https://www.microsoft.com/en-sg/learning/course.aspx?cid=20533
This concludes this post by David Papkin about Managing Virtual Networks using Microsoft Azure