THIS DAVID PAPKIN PAGE INFO on MICROSOFT AZURE SC-200 COURSE
Microsoft Certified: Security Operations Analyst Associate
Investigate, search for, and mitigate threats using Microsoft Sentinel, Microsoft Defender for Cloud, and Microsoft 365 Defender – Integrated cyberthreat protection for your email and collaboration tools.
Investigate incidents in the Microsoft Defender portal
Microsoft Sentinel – a scalable, cloud-native security information and event management (SIEM) that delivers an intelligent and comprehensive solution for SIEM and security orchestration, automation, and response (SOAR). Microsoft Sentinel provides cyberthreat detection, investigation, response, and proactive hunting, with a bird’s-eye view across your enterprise.
Microsoft Defender for Cloud – cloud-native application protection platform (CNAPP) that is made up of security measures and practices that are designed to protect cloud-based applications from various cyber threats and vulnerabilities.
Microsoft Defender XDR( Extended Detection and Response), a security platform that uses AI and automation to help organizations detect and respond to cyberattacks. It provides a holistic approach to cybersecurity by integrating detection, investigation, and response capabilities across a variety of domains.
Explore Extended Detection & Response (XDR) response use cases
Microsoft Purview is a comprehensive portfolio of products spanning data governance, data security, and risk and compliance solutions.
Learn about auditing solutions in Microsoft Purview
SOAR – Microsoft offers SOAR (Security Orchestration, Automation, and Response) capabilities primarily through Microsoft Sentinel, its cloud-native SIEM (Security Information and Event Management) and SOAR solution.
Key Features of Microsoft Sentinel SOAR Capabilities:
- Playbooks: Sentinel integrates with Azure Logic Apps to create playbooks that automate workflows for incident response. These playbooks can:
- Contain predefined steps for handling specific security events.
- Integrate with various third-party tools and Microsoft services for automated responses.
- Automation Rules: Allows the triggering of playbooks and other responses automatically when specific conditions in incidents or alerts are met.
- Threat Intelligence: Sentinel enables orchestration of threat intelligence for automated enrichment of alerts, providing more context for incident handling.
- Custom Connectors: Sentinel can connect to external APIs and systems to enable complex automations across hybrid environments.
SC-200 Courseware (Microsoft Learn)
KQL
KQL quick reference: https://docs.microsoft.com/en-us/azure/data-explorer/kql-quick-reference
Query best practices: https://docs.microsoft.com/en-us/azure/data-explorer/kusto/query/best-practices
Labs
SC-200 Interactive Simulations(6-22 are Sentinel related)
Logs
Set up a table with the Auxiliary plan in your Log Analytics workspace
Log sources to use for Auxiliary Logs ingestion(When to use Auxiliary Logs in Sentinel)
Demos
Detect and respond to modern attacks with unified SIEM and XDR capabilities(12 min)
Protect your organization with Microsoft 365 Defender(10 min)
Microsoft Defender for Identity(30 min)
How Microsoft Defender for Cloud Apps identifies and investigates risks(11 min)
Insider Risk Management(17 min)
Connect data to Microsoft Sentinel using data connectors(7 min)
Interactive Guide: Investigate and remediate threats with Microsoft Defender for Endpoint(17 min)
Safeguard your organization with Microsoft Defender for Office 365(28 min)
Interactive guide: Investigate and respond to attacks with Microsoft Defender for Identity(14 min)
Interactive Guide: Manage your Security Posture with Microsoft Defender for Cloud(19 min)
Interactive Guide: Threat and Vulnerability Management(13 min)
Interactive Guide: Detect and Respond to modern attacks with unified SIEM and XDR capabilities(12 min)
Videos
Microsoft Threat Protection – Incident management
Defender for Endpoint Automated Investigations
Microsoft Defender for Endpoint – Discover Devices
Microsoft Defender for Endpoint: Advanced hunting
Role-based access control – Microsoft Defender for Endpoint(5 min)
Microsoft Defender for Office 365(28 min)
Threat Analytics (4 min )
Threat Analytics (youtube 4 min)
Attack surface reduction – Microsoft Defender for Endpoint(7 min)
Microsoft Defender for Endpoint: EDR in block mode(4 min)
Microsoft Defender for Endpoint: Live response
Lab issues
Learning Path 3 – Lab 1 – Exercise 1 Enable Defender for Cloud
Task 4 . Make sure Extensions are installed by following this:
- Complete Task 4: Install Azure Arc on your on-premises server.
- Verify Connection: Ensure that WINServer shows a ‘Connected’ status in Azure Arc under Machines.
- Check Extensions: Confirm that the Defender extension is ‘Enabled’ and the Monitoring extension is ‘Installed’. If not, follow the steps below:
- Enable Monitoring Extension: Click on the WINServer machine, go to settings, and select Extensions.
- Install AzureMonitorWindowsAgent: Install the AzureMonitorWindowsAgent.
- Verify Installation: Check the Machines page to ensure the status has changed to ‘Installed’.
- Data Collection Rules: Log Analytics Workspace , Click on your workspace, then Agents.
- Follow from Step 6 of Task 5.
No Getting Started tab available. Task 5 not needed anymore.
Learning Path 4 – Lab 1 – Exercise 1 Creating queries for Sentinel using KQL
use https://aka.ms/lademo for All KQL queries
Learning Path6 – Lab 1 – Exercise 2 – Connect Windows devices to Sentinel
If “size unavailable for your subscription” error,
click “See all sizes”, D-series v6 and pick the cheapest one 2 vCPU and 8 GB Ram
Learning Path 7 – Lab 1 – Exercise 3 – Create a Scheduled Query from a template
Unable to create Incident rule.
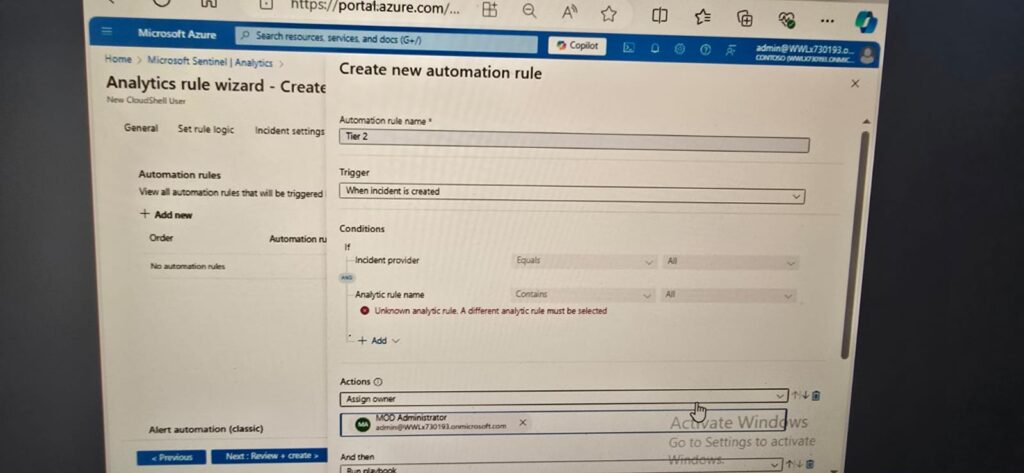
Create new automation rule – Step 31 Select Save. Gives error :” Analytic rule name “unknown analytic rule. a different analytic rule must be selected”
Helpful Azure learning links
Microsoft Cybersecurity Reference Architectures(MCRA)
Overview of Microsoft cloud security benchmark
Microsoft Learn –Microsoft Identity and Access Administrator
https://learn.microsoft.com/en-us/training/courses/sc-200t00
https://learn.microsoft.com/en-us/training/paths/implement-identity-management-solution/
Microsoft Certified: Identity and Access Administrator Associate
https://docs.microsoft.com/en-us/learn – Learn new skills and discover the power of Microsoft products with step-by-step guidance. Start your journey today by exploring our learning paths and modules.
Microsoft Azure Forums The Azure forums are very active. You can search the threads for a
specific area of interest. You can also browse categories like Azure Storage, Pricing
and Billing, Azure Virtual Machines, and Azure Migrate.
Azure Architecture Center Gain access to the Azure Application Architecture Guide,
Azure Reference Architectures, and the Cloud Design Patterns.
Microsoft Learning Community Blog Get the latest information the certification
tests and exam study groups.
https://channel9.msdn.com/ Channel 9 provides a wealth of informational videos, shows, and
events.
Azure Tuesdays With Corey Corey Sanders answers your questions about
Microsoft Azure – Virtual Machines, Web Sites, Mobile Services, Dev/Test etc.
Azure Fridays Join Scott Hanselman as he engages one-on-one with the engineers
who build the services that power Microsoft Azure as they demo capabilities,
answer Scott’s questions, and share their insights.
Microsoft Azure Blog Keep current on what’s happening in Azure, including what’s
now in preview, generally available, news & updates, and more.
End of David Papkin Microsoft Azure SC-200 page.
David Papkin favorite movies